# Typecho Blogging Platform
Typecho is a PHP-based blog software and is designed to be the most powerful blog engine in the world. Typecho is released under the GNU General Public License 2.0.
Link address:https://github.com/typecho/typecho/
This open source project has an XSS vulnerability, which can be exploited by attackers to obtain sensitive information such as cookies of a large number of users (including administrators), which is very harmful.
Affected versions:v1.2.1
# Environment Construction
- php 7.4.3
- MySQL 8.0.12
- Nginx 1.15.11
Download the source code file. After opening the environment, visit http://localhost:8191/ (the main directory of the project) and you will be redirected to the installation interface.
Click the button below to start the installation. In the initial configuration interface, make the following configurations. The advanced options are set to default.
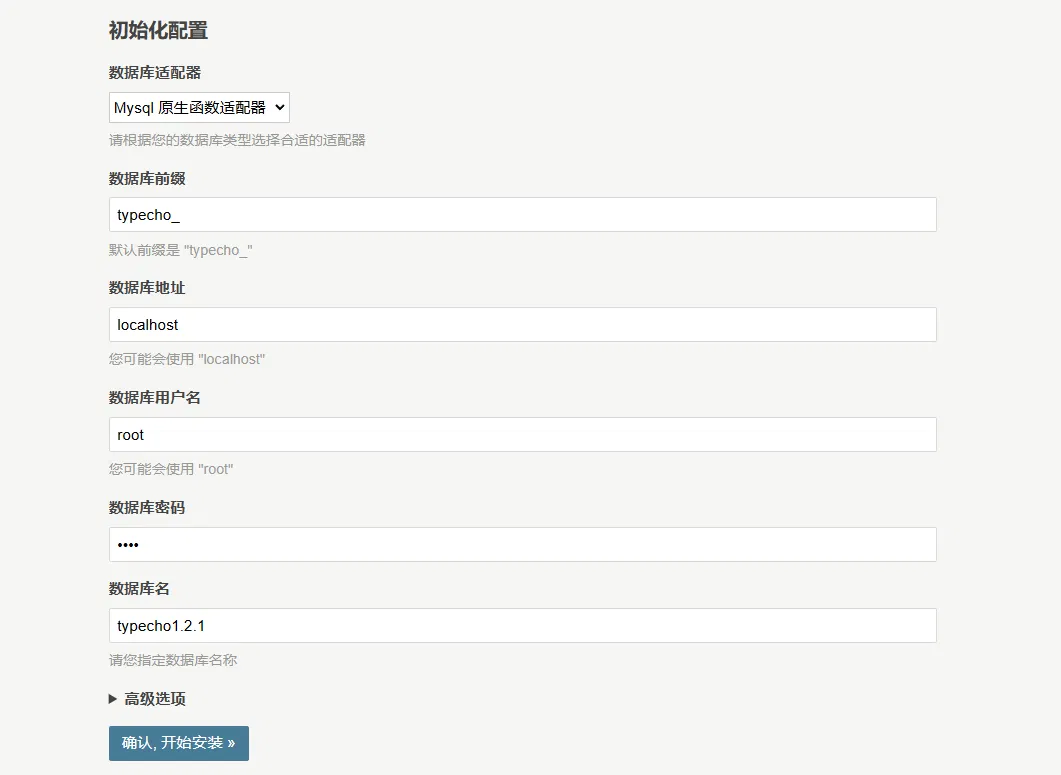
Before clicking to start the installation, you need to create the database typecho1.2.1
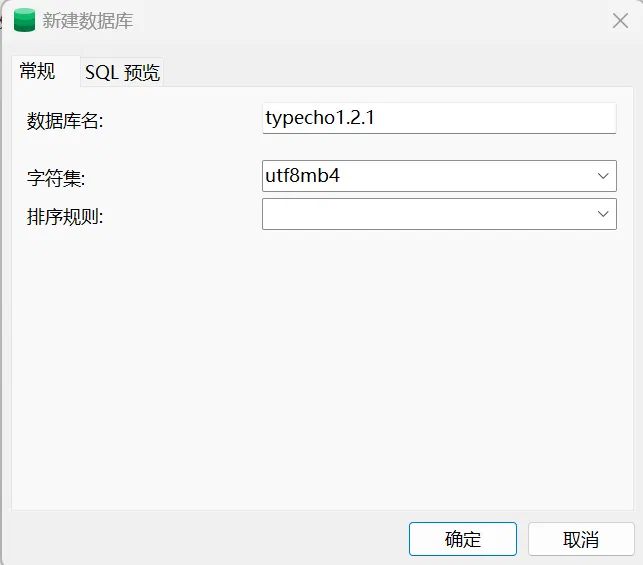
After creation, click Start Installation above, and set the administrator's account password and email address when creating an administrator account.
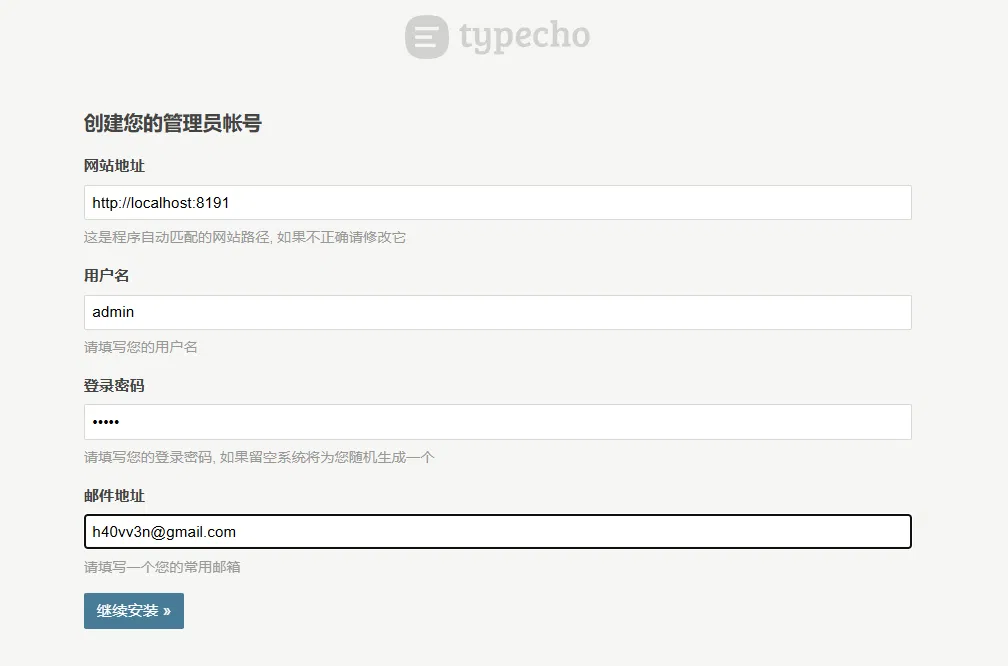
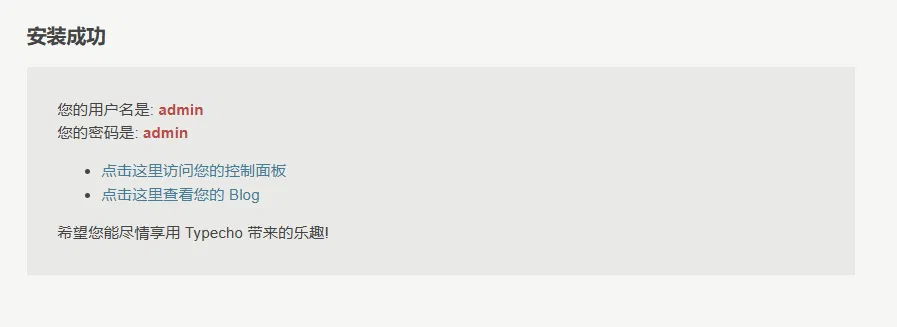
Click Continue to install. The installation is successful.
# Verification Process
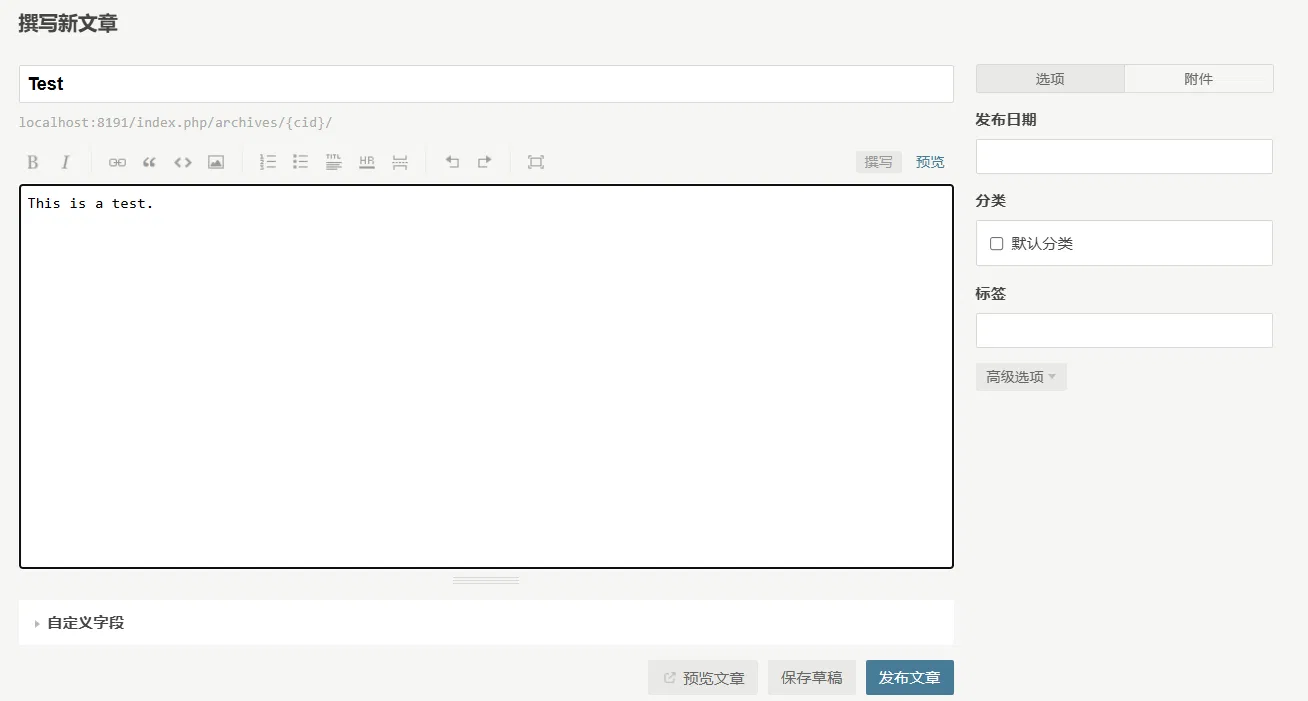
At this time, write an article directly and publish it
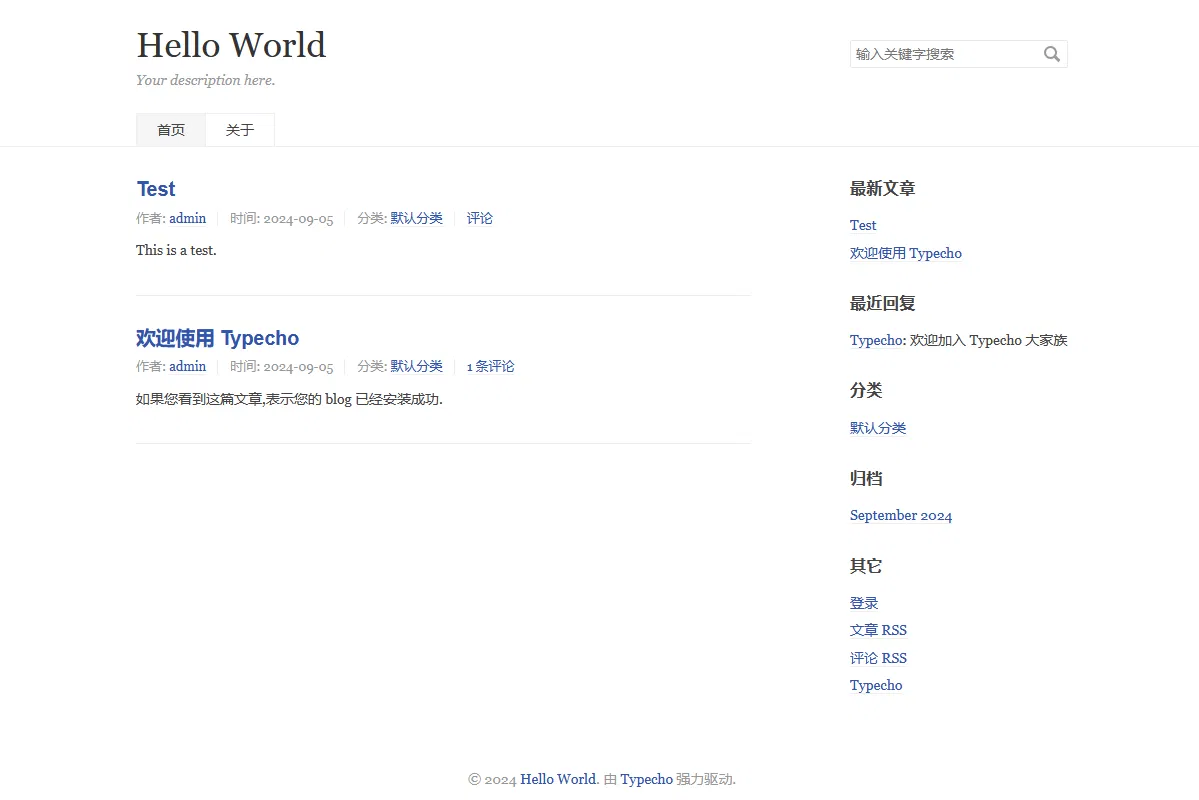
Then use another browser (simulating other users) to access the link http://localhost:8191/, and enter the article homepage of the admin user.
Click on the article just created by the admin user and make the following comment in it
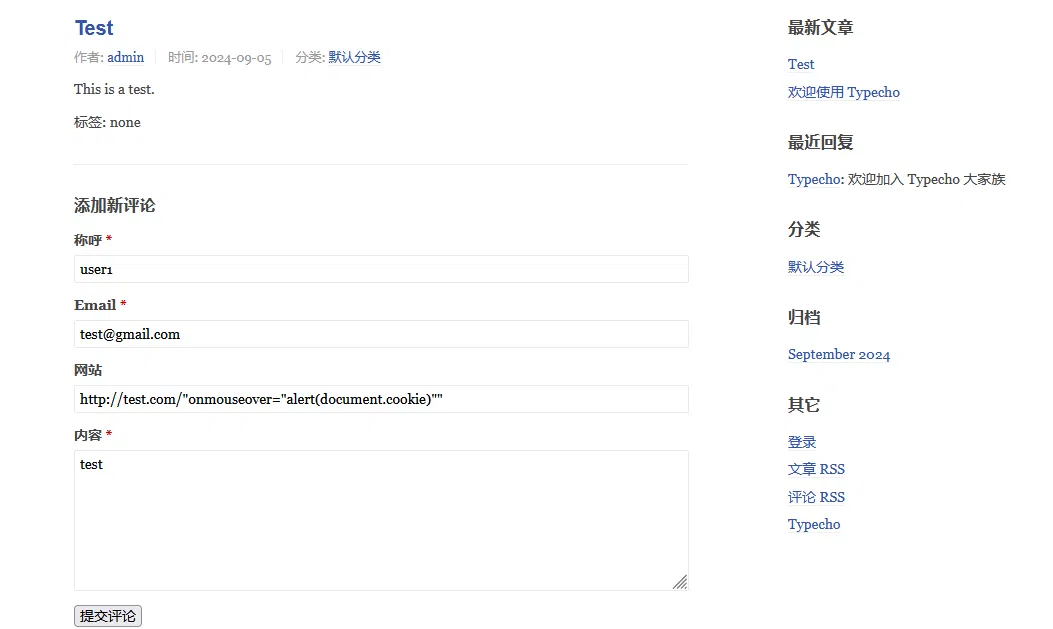
As you can see, an XSS attack is attempted at the website entry point. The POC is:
http://test.com/"onmouseover="alert(document.cookie)""
Comment submitted successfully
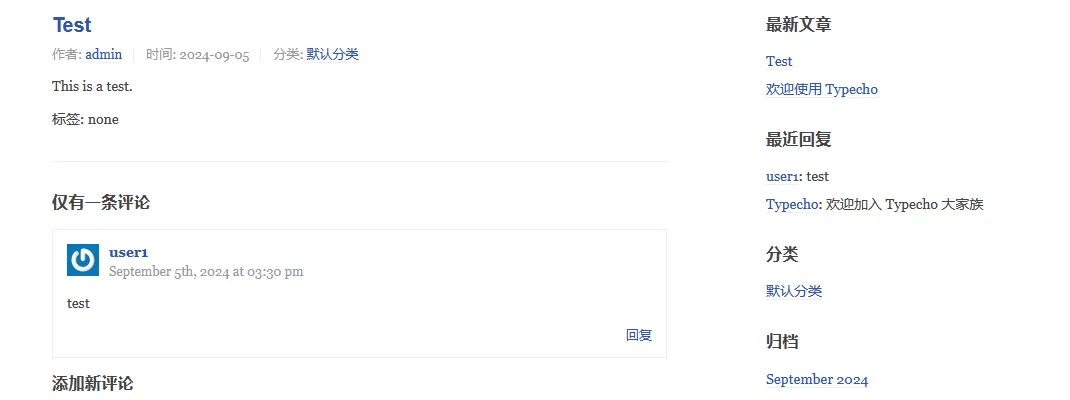
Now go back to the admin user's perspective and click Manage->Comments to display all the comments, including the comments submitted by the simulated user just now.
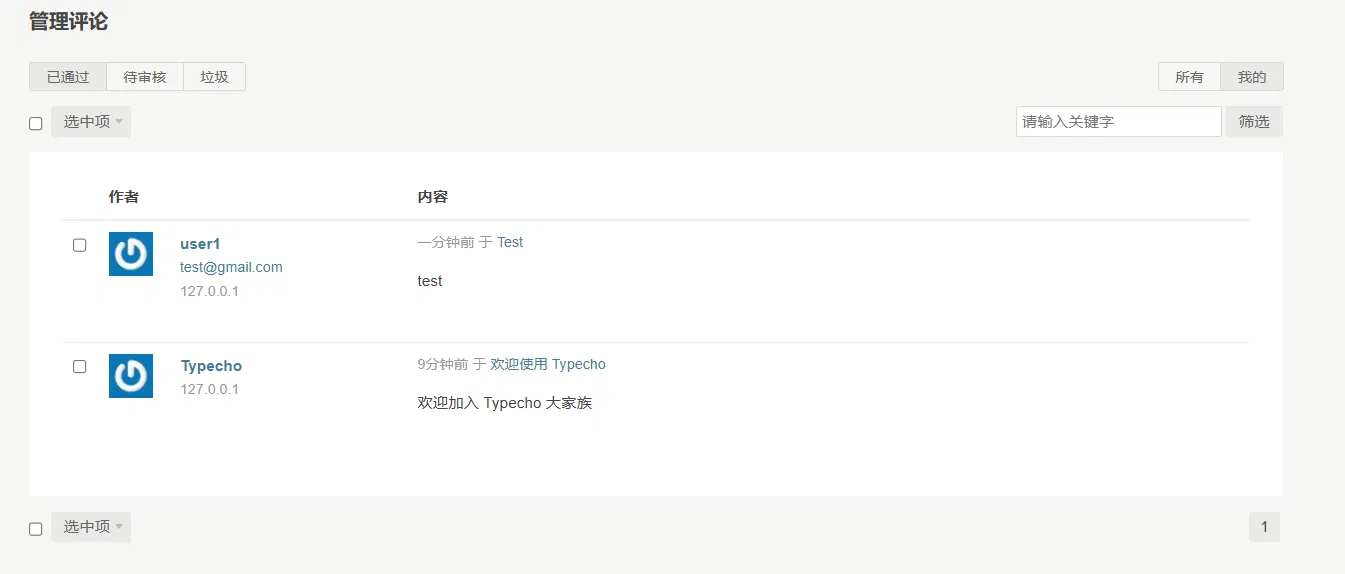
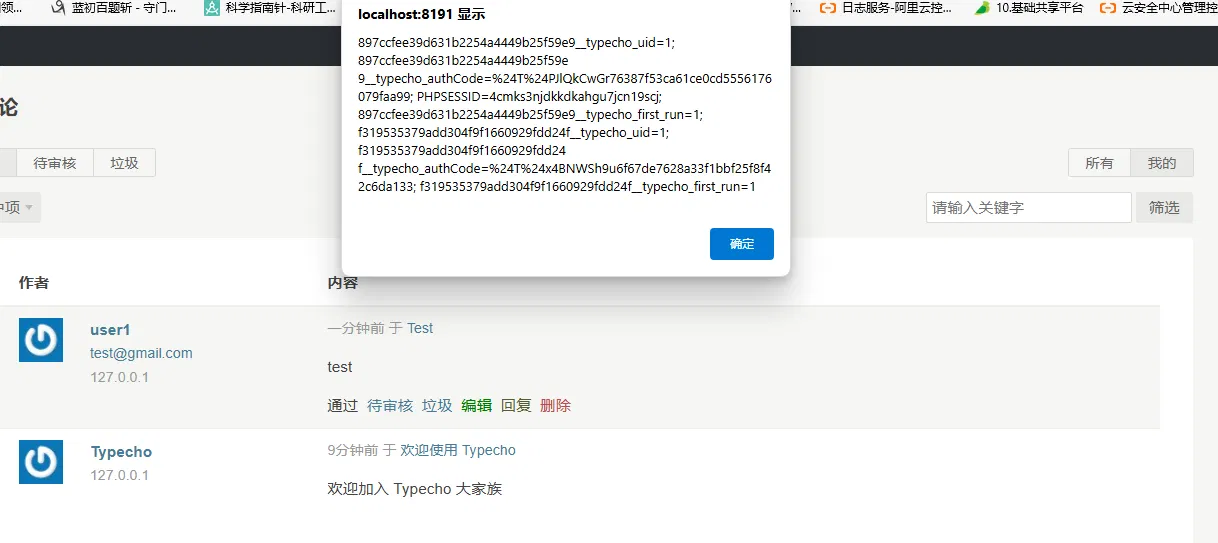
At this time, move the mouse over the name "user1" and you can see that the script is successfully executed and the cookie information is printed out.
# Summarize
At this point, it can be proved that there is an XSS vulnerability, which can be exploited by attackers to steal user information, spread worm viruses, etc., which is very harmful.